Cyber governance is failing, and CISOs are taking the fall. As ransomware surges and regulations tighten, boards are under pressure to prove they take cybersecurity seriously. But while directors demand answers, CISOs get fired, fined, or even prosecuted when things go wrong.
Enterprise leaders must confront a hard truth: today’s CISOs are caught between rising expectations and insufficient authority. They’re expected to reduce risk, ensure compliance, and safeguard reputation, and yet they often lack real control over budgets, infrastructure, third-party risk, or even employee behavior. In many breaches, they become the scapegoat for failures they couldn’t prevent.
This point of view draws a clear line. It defines what CISOs owe the board and, more importantly, what they don’t. If boards want real resilience and not just compliance checklists, they must stop outsourcing cyber risk to security leaders and start owning it at the top.
The modern CISO is tasked with enabling organizational resilience, defending brand trust, ensuring compliance, and mitigating business disruption. However, they rarely control the full set of levers needed to do any of that. Too often, CISOs are held responsible for risks they neither created nor can meaningfully influence.
Boards expect them to reduce risk but deny them the authority, staffing, budget, or enterprise-wide support required to achieve it. This is how security leaders become scapegoats for systemic failure. It’s a governance issue disguised as a performance one.
A mature cyber program starts by drawing a hard line between what CISOs can own and what they must escalate.
Under the CISO’s control:
Outside the CISO’s control:
Not all responsibilities are created equal, and not all deserve the same level of executive focus. To navigate this reality, CISOs must align their effort with their level of control and the task’s business impact.
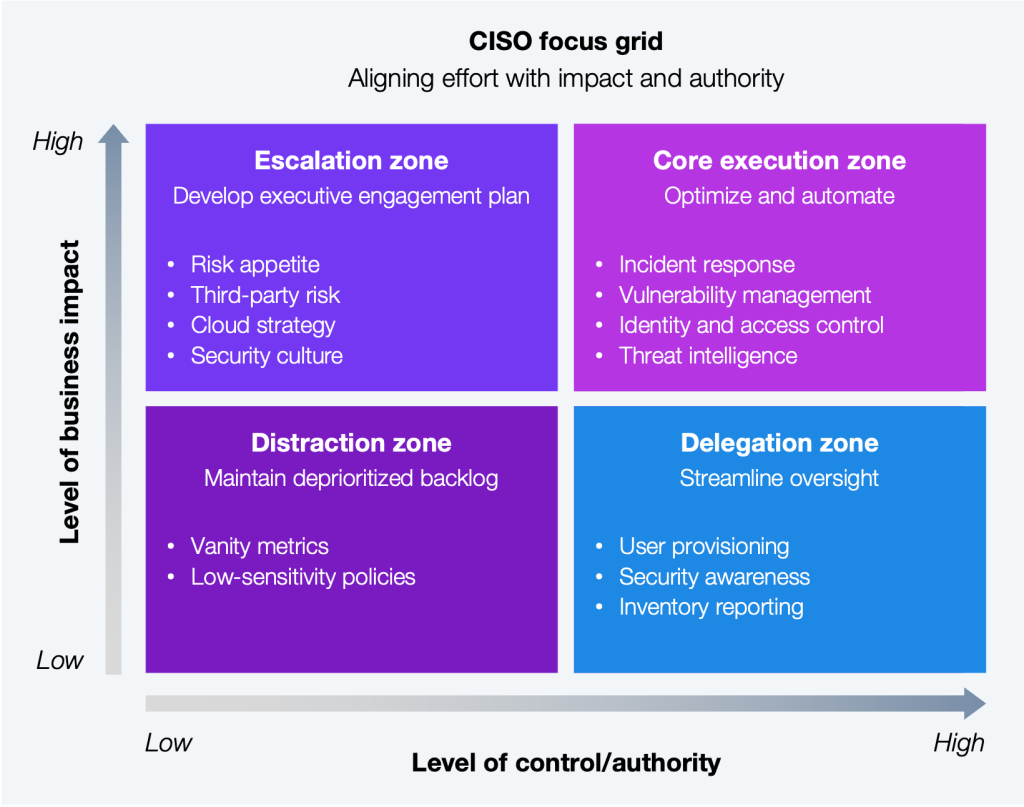
Source: HFS Research, 2025
CISOs should focus where they have control and where the stakes are highest:
Cybersecurity has outgrown the audit committee. Today, it’s a boardroom priority as central to business risk as financial controls, Environmental, Social, and Governance (ESG), or mergers and acquisitions (M&A). But most boards still treat it like a technical issue—one to delegate, not lead.
The regulatory environment has changed. Directors are now expected to understand cybersecurity, define risk appetite, and fund programs that go beyond minimum compliance.
What boards must do now:
The current cybersecurity scenario is about operational continuity, reputational trust, and the license to operate in regulated markets. There must be a shared responsibility model that defines what the CISO owns, what the board governs, and what must be led together.
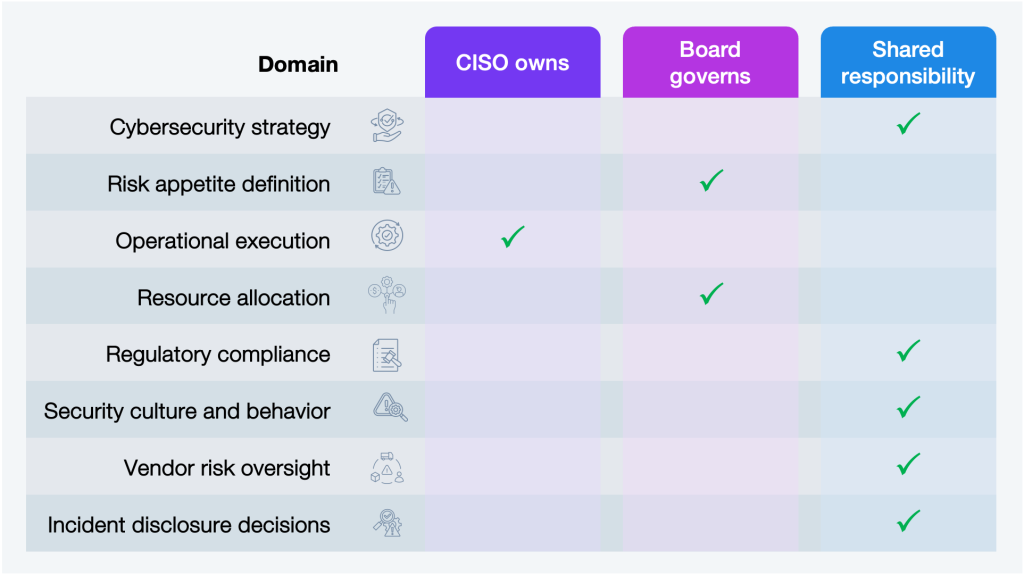
Source: HFS Research, 2025
If CISOs want board support, they must communicate in terms that matter at the executive level. Boards don’t want to hear about CVEs, firewalls, or SIEM logs. They want to know how cyber risk affects customers, operations, and the bottom line. This is not about dumbing things down but translating cyber risk into business relevance.
Use the metrics that actually matter
Cyber dashboards often overload boards with noise, i.e. long lists of vulnerabilities, tools, and acronyms that lack context. But this isn’t a board failure; it’s a communication failure. The CISO’s job is not to show everything but to curate a small, meaningful set of business-aligned indicators that drive clarity around risk, readiness, and resilience.
Here’s what boards should monitor:
CISOs and other security leaders should not overload the board. Instead, show trends, gaps, and how current performance compares to peers or accepted benchmarks.
Visual storytelling wins influence
Boards trust CISOs who communicate clearly, contextually, and candidly. Be direct about what’s improving and what’s still vulnerable.
Use dashboards, heatmaps, and red-yellow-green visuals. Don’t show raw patch data; show whether the business is trending toward or away from an acceptable risk level. The goal is not to impress; it’s to inform, and drive decisions.
Cybersecurity is now a boardroom obligation. Regulators worldwide are rewriting the rules, putting directors directly in the spotlight. What used to be delegated to the CISO is now a matter of personal liability and organizational accountability.
The regulatory wake-up call
These frameworks don’t just require reporting; they demand demonstrated governance.
CISOs don’t owe boards invulnerability. They owe clarity, foresight, and honest leadership. Boards, in turn, don’t owe CISOs passive oversight—they owe funding, authority, and shared accountability.
Cybersecurity cannot be treated as a delegated task or a compliance checkbox. It is a strategic business risk that demands joint ownership. Until boards define risk appetite and resource resilience and stop scapegoating CISOs for systemic gaps, their organizations will remain vulnerable—and their reputations at risk.
Enterprise leaders must move beyond blame and toward partnership. In today’s threat landscape, cyber risk is business risk, and survival is a shared responsibility.
Register now for immediate access of HFS' research, data and forward looking trends.
Get StartedIf you don't have an account, Register here |
Register now for immediate access of HFS' research, data and forward looking trends.
Get Started