Energy and utilities (E&U) firms accelerating the adoption of AI and other emerging technologies must recognize that cybersecurity is not just another layer to add but a responsibility. From AI-led customer engagement to digitalizing grid operations, the attack surface is expanding beyond traditional IT into operational technology (OT). The cybersecurity discussion can’t be isolated—it must be integrated into how the industry delivers clean, connected, and reliable energy. The same principle applies to the innovation required to meet the energy transition from fossil to decarbonized energy.
E&U organizations need a new level of collaboration—from the CIO and the COO to the CSCO, reaching all the way to the CEO and board level. Embedded cybersecurity based on that cross-organizational collaboration will mean innovation is empowered by governance that doesn’t overly restrict data access and analytics (see our separate E&U CIO agenda here).
To discover E&U’s best future self, including addressing some of the world’s biggest challenges, the sector must attract and retain talent capable of handling digital issues such as cybersecurity, decarbonization, and broader sustainability (as we explore here; in an industry not perceived as high tech or sustainable). Embedding cybersecurity into that talent and innovation agenda is fundamental.
Historically isolated, OT now intersects with cloud, edge, and AI-enabled systems—yet lacks the basic hygiene of enterprise IT. Still, cybersecurity is at the top of mind (see Exhibit 1), competing with the relentless efficiency drive.
Substations, pipelines, and control centers are suddenly internet-exposed but not cyber-hardened. Many legacy OT assets also run on outdated operating systems or proprietary protocols that lack native encryption or access control, creating soft targets for modern adversaries.
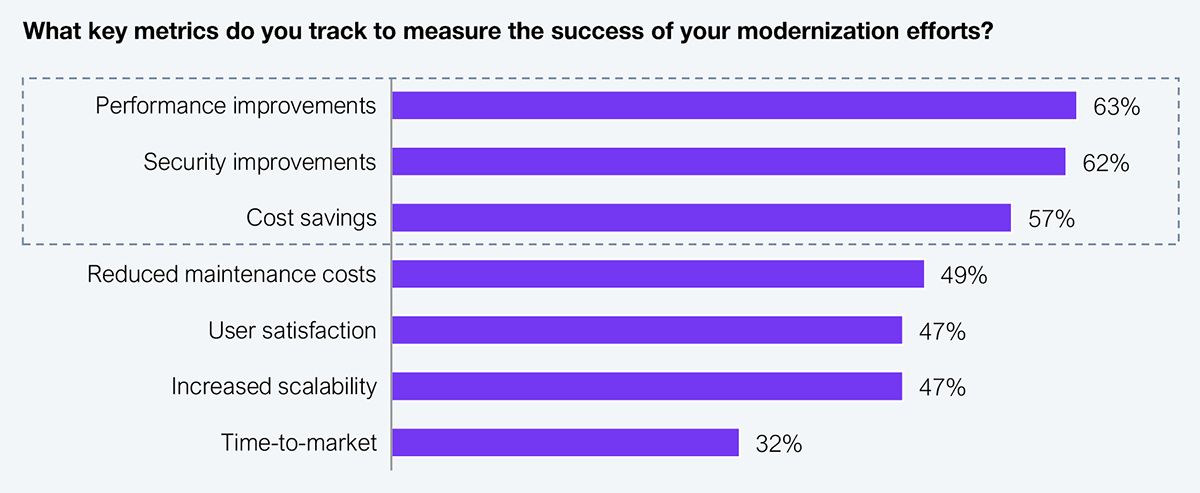
Sample: 90 energy and utilities executives from the Global 2000
Source: HFS Research, 2025
Some service providers are attempting to fill this gap with solutions from ’convergence-ready security architectures’ to ’vertical-specific’ cybersecurity offerings for refinery and plant-level operations. However, no provider solution matters if buyers don’t prioritize this internally.
Vulnerabilities such as shared credentials, unpatched systems, and training gaps are still common across critical infrastructure—putting lives, not just systems, at risk.
For instance, the Colonial Pipeline ransomware attack in 2021 forced the shutdown of a significant US fuel artery, leading to widespread stress and economic disruption. Similarly, the attempted poisoning of the Oldsmar water treatment plant in Florida underscored how remote access weaknesses can directly affect human safety.
The 2022 Sandworm attack on Ukraine’s grid wasn’t about data but turning off life-critical infrastructure. This wasn’t the only wake-up call. The 2020 Mumbai power outage, allegedly linked to foreign threat actors, disrupted one of India’s largest cities and highlighted the vulnerabilities of digitalized grid systems in emerging economies.
Digital trust is a precondition for digital progress. Embedded security must include:
Cyberattacks in E&U aren’t just economic—they’re ecological, political, and human.
The shift toward distributed energy resources (DER), smart meters, and microgrids increases the attack surface. Every new edge node from a rooftop solar inverter to a neighbourhood battery system introduces potential vulnerability.
Securing this complexity requires dynamic threat detection, authentication at the edge, and real-time visibility across energy ecosystems. Traditional perimeter security models won’t work when the grid is no longer a central system but a network of constantly shifting endpoints.
Cybersecurity will help grid decentralization scale more smoothly. It enables ’prosumer’ participation, bidirectional energy flows, and predictive balancing of supply and demand. Without strong cyber foundations, decentralization will be fragile and disguised as progress.
Cyber can’t be considered a cost center or a compliance checkbox. It is a core enabler of modern energy operations, i.e., from predictive grid control to autonomous maintenance and smart meter rollouts. It can enable resilient AI, smart grids and more intelligent automation of all industry and internal business processes.
Without embedded security, the innovation potential of these technologies will always be limited and held back by risk concerns or excessive governance. This is especially true in distributed energy environments, where real-time decisions span widely dispersed infrastructure. Secure-by-design systems enable these decentralized, data-driven networks to function safely and at scale.
It’s not enough to protect and detect. Energy providers must be built to recover. Ransomware, DDoS attacks, and firmware tampering are expected but not rare. The real test is whether you can isolate the threat, restore operations quickly, and limit disruption.
In the energy sector, that means testing failover systems, validating backup grid modes, conducting cyber-physical drills, and setting up manual control options in advance. Cyber resilience must be as tangible as black-start plans or storm contingencies.
Global standards such as NERC CIP (North America), NIS2 (EU), and IACS (automation systems) reflect increasing regulatory pressure. The US Transportation Security Administration (TSA) directives for pipeline security and the EU’s Digital Operational Resilience Act (DORA) push operators toward a more proactive security posture.
But regulation does not equal resilience. Actual enterprise readiness demands proactive threat modeling, regular stress-testing of incident response plans, OT-specific tabletop exercises, and executive alignment on risk. It’s about building systems that can withstand attacks, recover, and adapt across operations, partners, and vendors throughout the supply chain.
Digital transformation of any kind in E&U without embedded cybersecurity isn’t progress. It’s exposure for all of us.
Through deep collaboration across enterprise leaders and by ensuring the highest levels of talent are attracted and retained, the E&U sector must:
The next decade of energy innovation, from electrified fleets to dynamic pricing models and prosumer marketplaces, depends on trust in every digital touchpoint. Cybersecurity is not a brake on innovation. It keeps the engine running safely, no matter how fast the sector moves.
Register now for immediate access of HFS' research, data and forward looking trends.
Get StartedIf you don't have an account, Register here |
Register now for immediate access of HFS' research, data and forward looking trends.
Get Started