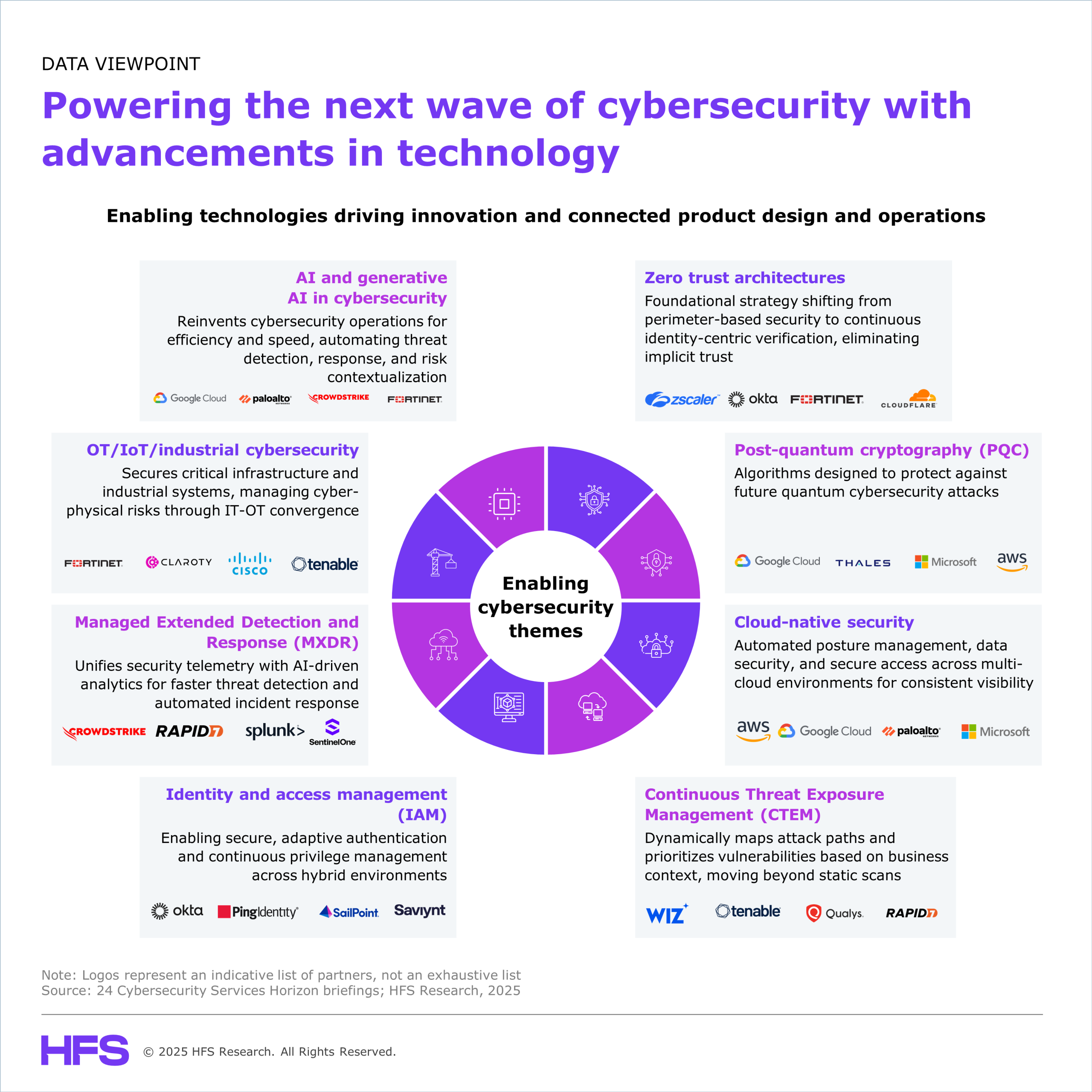
Cybersecurity is entering a transformative era, driven by the convergence of advanced technologies and a rapidly evolving threat landscape. As digital ecosystems grow, organizations must evolve beyond reactive protection and adopt proactive strategies that secure assets, meet compliance goals, and sustain business resilience.
Service providers are responding by embedding emerging technologies across detection, response, identity, and risk workflows. AI and generative AI enhance detection, risk triage, and response through faster analysis, contextual insight, and automation. At the same time, providers are modernizing their architectures through cloud-native platforms, zero trust enforcement, and quantum-safe cryptography to deliver secure access, unified visibility, and cryptographic agility at scale.
- AI, GenAI, and automation drive smarter, faster, and more adaptive cyber defense by enabling intelligent detection, LLM-assisted triage, synthetic threat simulation, and faster incident response across distributed environments. These technologies transform security operations, enabling real-time anomaly detection and adaptive defense against increasingly sophisticated and automated cyber threats.
- Cloud-native security, zero trust, and post-quantum cryptography are forming the backbone of modern enterprise defense. The shift to cloud-native platforms enables integrated telemetry, dynamic workload protection, and policy enforcement at scale. Zero trust architectures support continuous identity validation and risk-aware access across hybrid environments. At the same time, post-quantum cryptography is helping organizations strengthen data protection and prepare for future cryptographic risks by aligning with emerging compliance expectations and encryption standards.
- Securing the expanding digital ecosystem across OT/IoT, identity, and proactive exposure management is now mission-critical. The convergence of IT, OT, and IoT environments demands specialized protection built on real-time asset intelligence, segmentation, and protocol-aware visibility. Modern Identity and access management (IAM) platforms provide contextual access control and lifecycle governance to reduce privilege risks across hybrid enterprises. Continuous Threat Exposure Management (CTEM) enables organizations to map exposures, prioritize vulnerabilities, and drive risk-informed remediation. Managed Extended Detection and Response (MXDR) solutions unify telemetry, automate response workflows, and strengthen threat coverage across endpoints, cloud, and identity layers.
The Bottom Line: From GenAI to quantum readiness, cybersecurity is becoming more intelligent, modular, and business-aligned.
Cybersecurity is fundamentally transforming as service providers adopt enabling technologies to combat an increasingly complex threat landscape. Enterprises proactively adopting these innovations will be best positioned to build resilience, ensure compliance, and allow secure digital growth in the years ahead.
