Preventing breaches is no longer the primary focus for chief information security officers (CISOs). Instead, their priority must be to ensure that cybersecurity enables business continuity and effectively manages real-time risks. The HFS Horizons: Cybersecurity Services, 2025 study, which evaluated 24 service providers and captured insights from cybersecurity clients and ecosystem partners, underscored that cybersecurity must evolve with the business.
In the recent HFS Pulse study, 40% of enterprise leaders cited cyber threats as a top external barrier to achieving business priorities (see Exhibit 1). The need to embed cybersecurity into strategic decision-making has never been more urgent. Among the top three barriers, cybersecurity is the one leaders can directly influence, making it the most immediate lever for enabling enterprise growth.
For CISOs, the challenge is transforming cybersecurity into a strategic enabler of business trust, resilience, and growth. This report explores how enterprise expectations have matured, what truly sets providers apart, and how CISOs can equip their companies for the evolving threat landscape.
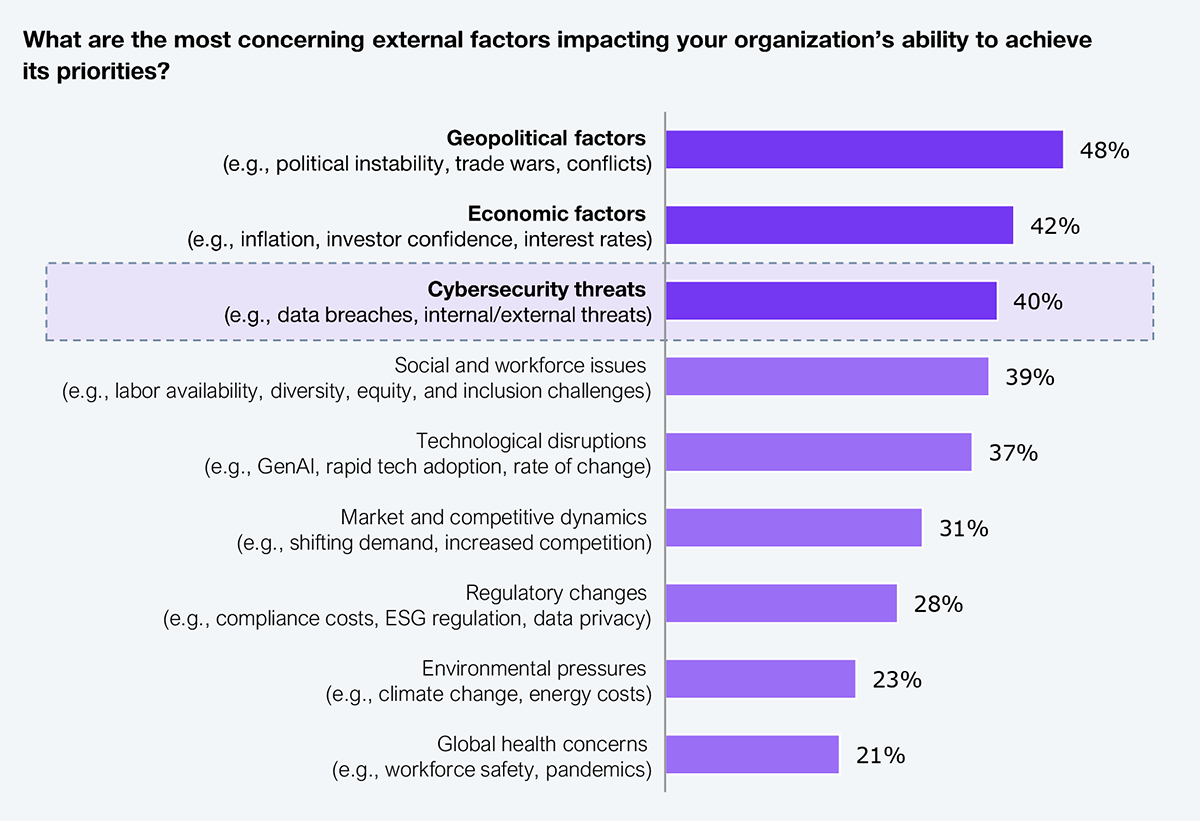
Sample: 305 major enterprise decision-makers selected their top three factors
Source: HFS Research Pulse, 2025
Enterprise buyers demand outcomes, not just fatigued alert dashboards. The definition of cybersecurity success has evolved from counting blocked threats to proving how well and quickly the business is protected and recovers. The focus has moved to maintaining uptime, meeting regulatory obligations, and safeguarding customer trust. Identity has also become a new perimeter, with adaptive IAM (identity and access management) and authentication anchoring enterprise trust. These KPIs (key performance indicators) are increasingly written directly into cybersecurity SLAs (service level agreements).
Cyber resilience also demands accountability. Detection alone is not enough. Enterprises expect providers to co-own incidents, move beyond ticketing, and deliver SLA-bound remediation and real-time advisory. That’s what separates a vendor from a strategic partner. Moreover, given their complex, multi-regional footprints, cybersecurity services must be modular and tailored to geography, industry, and risk profile without breaking interoperability. To manage this complexity, buyers consolidate to fewer, more accountable partners who can deliver consistency and cost efficiency. The one-size-fits-all MSSP (managed security service provider) model has reached its limits, and enterprises increasingly demand security components they can plug in or swap out without re-architecting the entire infrastructure.
The number of tools cybersecurity providers offer no longer defines the leaders; it’s their ability to orchestrate them into cohesive, outcome-driven platforms. Platformization is reshaping service delivery, as top providers unify threat detection, identity, cloud posture, and compliance into integrated platforms. The results are streamlined operations, contextualized risk, and decision support for the business.
Differentiation also comes from verticalization. Energy and utilities, healthcare, banking, and manufacturing enterprises face regulatory pressures and threat scenarios. To meet sector-specific demands, providers are leaning into their deep domain expertise and offering pre-built, industry-specific frameworks to ensure compliance readiness, deliver targeted protection, and accelerate time to value. Combined with platformization, verticalization can reshape business-aligned cybersecurity outcomes.
Providers that turn innovation into execution stand apart. A recent HFS report identified emerging technologies and themes driving innovation across cybersecurity services. By embedding these capabilities into repeatable services, providers give enterprises the confidence that cybersecurity investments will protect performance and accelerate growth.
Enterprises expect GenAI (generative artificial intelligence) protections embedded in workflows, model governance built into deployment pipelines, and quantum-safe cryptography delivered at scale. The leaders co-innovate with clients and industrialize these capabilities into repeatable, scalable services that deliver consistent outcomes. Continuous threat exposure management (CTEM) has also become a defining marker of maturity, separating providers that can prioritize exposures from those that rely on periodic scans.
Securing AI is now a top priority in enterprise buying decisions. With advanced AI tools embedded in workflows, the attack surface has shifted to prompts, models, and data pipelines. Enterprises also ask how providers will safeguard the AI systems running the business. That includes preventing data leakage, model manipulation, hallucination-based misinformation, and enforcing guardrails over how LLMs (large language models) are trained, governed, and deployed.
AI is both the heart of the solution and the root of the problem. For attackers, GenAI accelerates deepfake impersonations, vulnerability discovery, and automated exploitation at scale. For defenders, AI transforms cybersecurity from reactive monitoring to intelligent anticipation. Enterprises expect providers to operationalize AI in their platforms for faster detection, orchestrated response, and reduced mean time to resolution.
Business continuity requires the convergence of people, platforms, and predictive insights. The attack surface expands as enterprises embrace AI, decentralized infrastructure, and cyber-physical convergence, making it imperative for CISOs to adopt modular architectures, automate threat management, and secure AI ecosystems.
Service providers, in turn, must evolve their cybersecurity strategies, including delivery models and go-to-market strategies, as per business needs to provide outcome-based services. In short, enterprises that partner with providers that co-create, adapt, and execute in this dynamic environment will be best positioned to stay ahead of threats.
Cybersecurity is the backbone of enterprise trust and must be a strategic enabler. As threats grow more complex and AI brings promise and new vulnerabilities, the role of cybersecurity has fundamentally changed. Enterprises should expect nothing less than proof that cybersecurity investments protect business performance and enable growth.
Register now for immediate access of HFS' research, data and forward looking trends.
Get StartedIf you don't have an account, Register here |
Register now for immediate access of HFS' research, data and forward looking trends.
Get Started